What is the Secret to Building Valuable Tokens?
What are Token Architectures?
Architecture is both the process and the product of planning and designing structures, while tokens represent assets or utility on a blockchain, which is a decentralised ledger or database. Token architecture is thus both the process and product of planning and designing token structures, where stakeholders exchange value in the form of a token within a predefined framework of incentive mechanisms, with the aim of maximising utility for all stakeholders and aligning individual incentives with network objectives.
Figure 2: An example of a Token Architecture
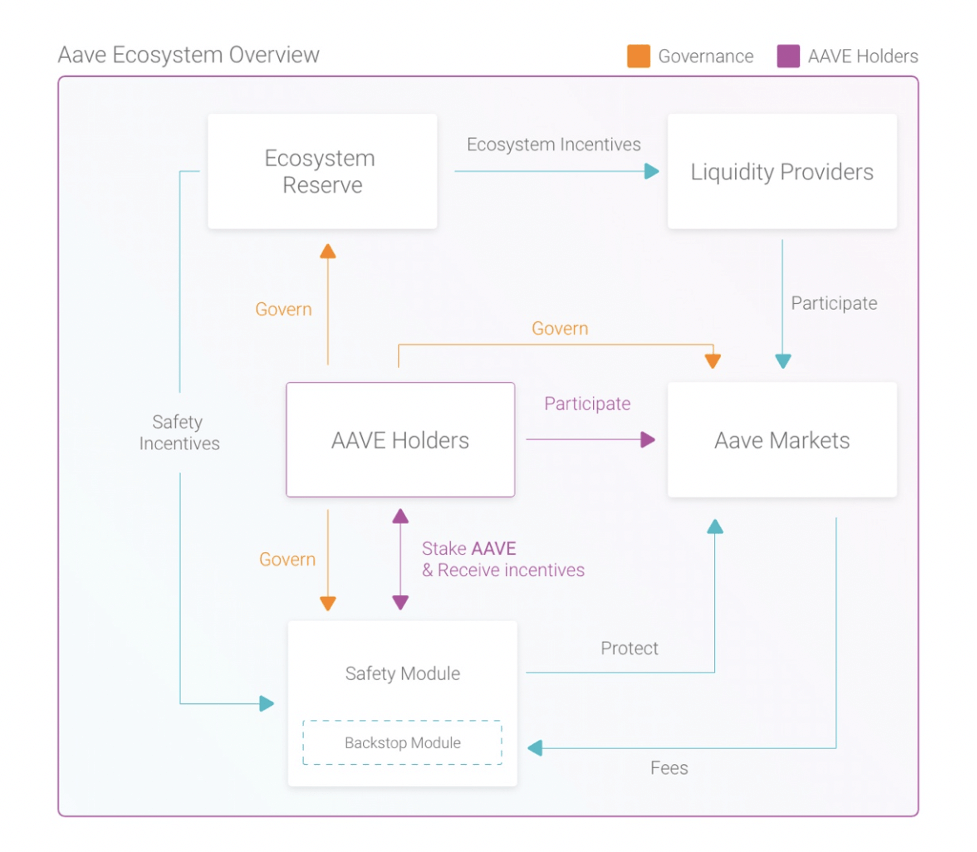 Source: https://docs.aave.com/aavenomics/ecosystem-overview
Source: https://docs.aave.com/aavenomics/ecosystem-overview
Token Architecture as a Process
First, let’s focus on token architecture as a process of designing token structures. A lot of work has been done on the workflow of creating token architectures. Eden Dhaliwal of Outlier Ventures wrote the 3Ds of Token Ecosystem Creation in 2018 and the Token Engineering movement pioneered the use of complex system engineering software to simulate, optimize and validate parameters of token architectures. Borrowing from the 3Ds framework, the token architecture process consists of:
- Token Discovery: Outlines the key characteristics of a token architecture.
- Token Design: Optimises and validates the key parameters of a token architecture.
- Token Deployment: Implements a token architecture into a crypto protocol’s core business model.
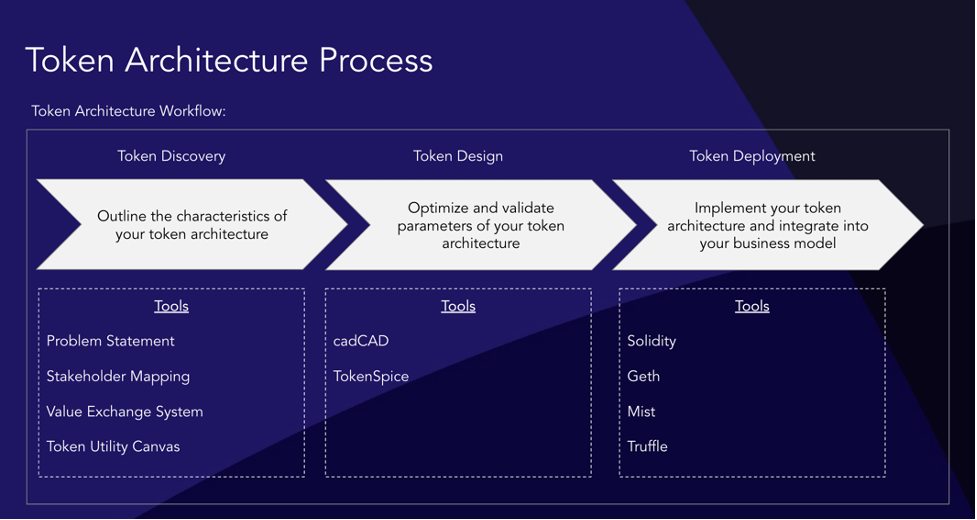
Source: OV Internal Analysis
If you haven’t read the 3Ds, here is a quick recap of Token Discovery:
- Step 1: Think about the problem that the token should be solving, i.e. what exact value / functionality will the token be adding to the business model / value proposition of its crypto protocol. For example, in the case of Aave, the AAVE token solves the problem of decentralized governance, and derisks the protocol via the Safety Module.
- Step 2: Think about all the different behaviours people are expected to exhibit in the value chain, and use this behaviour framework to divide these people into differentiated stakeholder groups. In the case of Aave, there are AAVE token holders, Liquidity Providers and Users.
- Step 3: Come back to the problem defined in Step 1, with various stakeholder groups in mind, and design the mechanisms that will direct the stakeholders towards solving the problem. Bear in mind that different stakeholder groups often have conflicting interests and the main goal here is to design mechanisms that make stakeholders work together for the benefit of the crypto protocol. For example, Aave is using mechanisms such as the Ecosystem Reserve, Safety Module, Backstop Module and Aave Markets to achieve this goal.
- Step 4: Translate all of the above into a graphic representation of the value exchange system, which serves well for communicating the high level ideas behind the token. Please see Figure 2 for Aave’s graphic representation of its value exchange system (token architecture).
If you’re interested in tools and details on later stages of the process, go check out the 3Ds of Token Ecosystem Creation. We’re going to focus on Step 3 for the remainder of this article, namely what mechanisms can we use to address the problem statement. One of the main goals of mechanism design in token architectures is to optimize token value, which is the primary driver of token price. Therefore, before we jump into the actual mechanisms, we need to have a look at what constitutes the value of tokens and what the key drivers of token price and token value in token architectures are.
Decomposing Token Value & Token Price
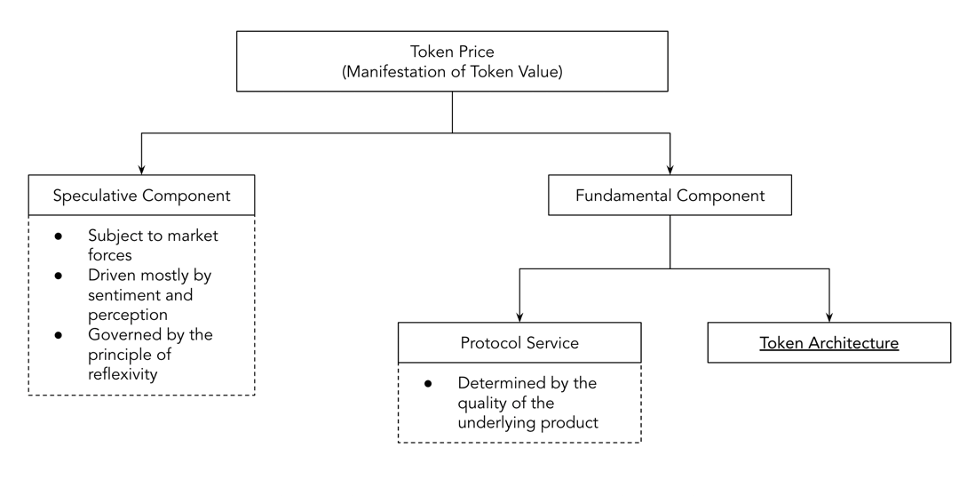 Source: OV Internal Analysis
Source: OV Internal Analysis
Token value implies the utility or worth of the crypto protocol token. Token price is merely a numerical manifestation of value for which buyers are willing to buy and sellers sell tokens at any given time. Compared to token price, token value is a more elusive concept. Token value can be different for different stakeholders depending on their specific needs and wants. Token price is generally driven by sentiment based on perceived token value. Too much focus on maintaining token price may seem unnecessary, but high token price is integral to the success of any crypto protocol for multiple reasons, with the primary ones being security for the protocol and profitability for stakeholders. The higher the token price, the harder it is to attack its crypto protocol. Token price can be decomposed into 2 components:
- Speculative Component
- Fundamental Component
Speculative Component of Token Price
The speculative component is subject to market forces, driven mostly by sentiment and perception. No matter the present utility of the crypto protocol and its tokens, if demand on the secondary market outweighs supply, the market price of a token will rise. Token architecture choices don’t play a direct role here, but can have a significant impact on token price through the laws of reflexivity, as defined by George Soros. The key to managing the speculative component of token price is to ensure high liquidity by using market makers on centralised exchanges and deep liquidity pools on decentralised exchanges. It is important to note that currently the vast majority of prices of crypto assets are made up mostly of the speculative component. This can be contrasted with e.g. real estate, where the fundamentals and utility of assets are much clearer and much easier to value than in the case of cryptoassets, which makes it less driven by speculations and more by fundamentals.
Fundamental Component of Token Price
The Fundamental Component of Token Price is the value attributed to the token based on the fundamental value it offers to stakeholders. This fundamental value generally comes from 2 sources:
1. Protocol Service
2. Token Architecture
The utility or usefulness of the protocol service is determined by the quality of underlying product and product market fit. This can be low slippage on major decentralised exchanges like Uniswap or cheap storage on decentralised storage protocols like Filecoin. If stakeholders find the product valuable and the token is tied into this value, the demand for the token will rise. Token architecture on the other hand focuses on the mechanisms that increase the fundamental value of the token. We previously defined token architecture as a process, now let’s look at it as a product.
Token Architecture as a Product
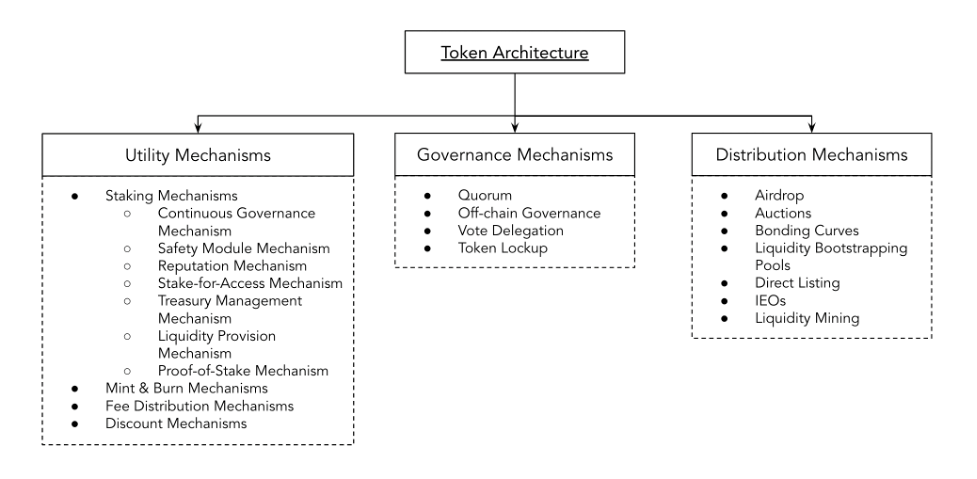
Source: OV Internal Analysis
*Note: This blog post only analyzes token architecture utility mechanisms, governance and distribution mechanisms will be analyzed in later posts.
Token architectures are structures consisting of stakeholders that interact with themselves and the crypto protocol via mechanisms. Mechanisms are systems working for a goal, or using a strictly engineering definition, devices that transform input forces and movement into a desired set of output forces and movement. Based on observations of the wider crypto market in early 2021, the vast majority of token architectures exhibit 3 types of mechanisms:
- Utility Mechanisms (explored in this blog post)
- Governance Mechanisms (to be explored in future blog posts)
- Distribution Mechanisms (to be explored in future blog posts)
Utility Mechanisms in Token Architectures
Before we dive deep into individual utility mechanisms, we need to understand the distinction between productive and non-productive tokens (as defined by Placeholder VC here), because their value is driven by different factors.
Non-productive tokens are those that behave like commodities in traditional finance. Non-productive tokens can be valued using the equation of exchange (MV = PQ), where monetary level (M) multiplied by velocity (V) equals price multiplied by quantity (PQ). The PQ side of the equation represents the value of protocol service, the MV side of the equation represents monetary value of the tokens multiplied velocity. Token velocity denotes the number of times a token changes hands within a certain period of time. If we keep PQ constant and lower V, we end up with higher M, essentially with higher token price. Effective utility mechanisms are those that lower token velocity (V) or increase the utility of the protocol service (PQ) or ideally both simultaneously. In non-productive tokens, the key to effective utility mechanisms is to design and implement mechanisms that increase the fundamental value of the token, while reducing the token velocity. This can be achieved via mechanisms such as:
- Staking Mechanisms: Reduce circulating supply in relation to the total supply of tokens.
- Mint & Burn Mechanisms: Reduce the total supply of tokens.
Productive tokens are those that resemble debt or equity in traditional finance, for example by having in-built voting mechanisms or offering yields under certain circumstances. The value of productive tokens can be calculated as the net present value (NPV) of annual value flows to token holders, in a similar way to how capital assets in traditional finance are valued. In productive tokens, the key to effective utility mechanisms is to design and implement mechanisms that increase the value flows to token holders. This can be achieved via mechanisms such as:
- Fee Distribution Mechanisms: Implement or increase fee distribution to token holders.
- Discount Mechanisms: Implement a discount mechanism into the token, which would let users pay less for the underlying utility of the protocol than they would if they did not own / use the token.
It is important to note that most tokens are both productive and non-productive, and their token architectures can be positively impacted by implementing any of the above mentioned mechanisms.
Staking Mechanisms
The way circulating supply is reduced in relation to the total supply is usually via introduction of a staking mechanism. Staking mechanisms reduce the average velocity of tokens and often provide additional security to the protocol. Filecoin is a decentralized network for sharing idle storage resources. If stakeholders have an unused hard disk, they can plug it into the network, become storage providers, other stakeholders can use the storage and the storage providers get paid. But in order to provide storage to the protocol, storage providers are required to stake a certain amount of Filecoin tokens into the protocol. This mechanism has a wide range of positive consequences for its token architecture, such as that it creates buy pressure for the token because in order to be able to provide your storage resources to Filecoin, storage providers first need to buy some Filecoin tokens. It also reduces the velocity of the token, because storage providers need to stake the tokens before participating, and it prevents storage providers from behaving in a malicious way, because if they do, they are going to lose their staked tokens. The main types of staking mechanisms that can be seen being used by crypto protocols right now include:
- Continuous Governance Mechanism: Incentivises token holders to keep their governance tokens staked continuously in order to maximise their voting power. A proposal is usually a smart contract where token holders stake tokens to express their agreement with the proposal. Each proposal needs to reach a certain threshold within a predefined period of time. If token holders want to use their tokens to vote on another proposal, they first need to unstake their tokens from the previous one. It is currently used by MakerDAO.
- Safety Module Mechanism: Incentivises token holders to stake their tokens into a smart contract called Safety Module in order to earn yields on their staked tokens, while allowing the tokens to be used as a safety buffer, should the protocol become insolvent. In case of a financial shortfall, a certain amount of tokens staked in the Safety Module are auctioned off and used to compensate protocol losses. Safety Modules have been pioneered by Aave.
- Reputation Mechanism: Incentivises token holders to stake their tokens in order to earn yields on their staked tokens, while providing a source of truth to the crypto protocol. The power and relevance of the “truth” is usually indicated by the value of the staked tokens. This mechanism is currently used by Augur and Chainlink.
- Stake-for-Access Mechanism: Requires token holders to stake a certain amount of tokens in order to participate in the network, or gain access to the utility of the network. It is usually used with the aim to prevent spamming of the network. The most prominent examples include crypto protocols like Filecoin or Cudos.
- Treasury Management Mechanism: Allows for the use of the crypto protocol treasury as a mechanism with the power to take out or buy out tokens out of circulating supply. This mechanism is planned to be used by Axies Infinity or KeyTango.
- Liquidity Provision Mechanism: Lets token holders lock tokens in the protocol and serve as a source of liquidity for automated market makers and lending and borrowing protocols in DeFi, such as Balancer or Uniswap. This mechanism does not require the use of the protocol’s native token, i.e. if token holders want to provide liquidity to Uniswap or Balancer, they don’t need to do it via their native tokens UNI and BAL, they can create any token pair they want. It is therefore not particularly interesting from a token design perspective and is only included for completeness.
- Proof-of-Stake Mechanism: Secures layer 0 and layer 1 protocols, used by Ethereum 2.0, Cosmos, Solana, Polkadot or Near. The Proof-of-Stake consensus mechanism uses a pseudo-random election process to select a node to be the validator of the next block, based on a combination of factors that could include the staking age, randomization, and the node’s wealth. This mechanism is only relevant for layer 0 and layer 1 protocols.
If stakeholders are financially rewarded for locking up their tokens, a major consideration is where the yield comes from. It can be either from the revenue of the crypto protocol (sustainable), from a premined pool of tokens (semi-sustainable) or from inflating the token supply (semi-sustainable).
Mint & Burn Mechanisms
Another way to reduce the velocity of crypto protocol tokens is to reduce the total supply of tokens, usually done by using Mint & Burn Mechanisms. These are mechanisms that (apart from minting) can burn a certain amount of tokens according to a predefined logic and thus increase scarcity of the token. In theory, the protocol ends up with fewer tokens chasing the same value. There are mixed opinions on to what extent this is beneficial for the protocol as a whole. Here is a great article by Placeholder VC advising against Mint & Burn Mechanisms.
Although reducing token velocity by reducing the total supply of tokens can be attractive for the reasons mentioned above, it sometimes interferes with the incentives of stakeholders (reduced profitability, etc). Token Architects need to be very aware of the tradeoff that they are making and balance the interests of different stakeholder groups. We will explore this problem in more detail in later blog posts.
Fee Distribution Mechanisms
Apart from reducing token velocity, we can also add additional layers of utility to the token. One way of doing this is implementing a fee distribution mechanism or, if the token already has one, increase the fees accrued on the token. One key consideration here is that financial incentives are one of the strongest incentives in token architectures and they should be used as much as possible to make stakeholders behave in the interest of the protocol. For example, SushiSwap distributes a portion of its DEX fees to token holders, but only to those who stake their tokens into the SushiSwap protocol.
Discount Mechanisms
Lastly, we can use tokens as discount vouchers applicable to the service of the protocol. Most tokens with this mechanism are tokens emitted by centralized exchanges. They give their holders a discount on trading fees, if they decide to pay them in the token. The most notable examples include Binance’s BNB token and FTX’s FTT token. Also, these tokens usually use the Burn Mechanism to further increase their value.
Conclusion and Next Steps
It is important to keep in mind that utility mechanisms which are fully functional in isolation can have destructive effects on our token architectures when combined with other functional mechanisms. Therefore, a significant component of the token architecture process is to understand how different mechanisms that we select for our token architectures interplay with each other. While this is usually the domain of token engineers, multiple software tools have recently been developed to help select, optimize and validate the mechanisms that you select for your token architecture. The easiest option is a software called cadCAD (stands for Complex Adaptive Dynamic Computer Aided Design), it was developed by a token engineering consulting company Blockscience and is maintained by a vibrant community. cadCAD is an open-source Python library that lets you design, optimize, validate and understand dynamical complex systems. It is useful because it allows engineers to ask powerful what if questions, using simulation features like A/B Tests, Parameter Sweeps or Monte Carlo Analysis. The team behind cadCAD has gone into great lengths to ensure that cadCAD is available to everyone and they recently released the first comprehensive online course via a platform called cadCADedu. You can check it out here.
Well done on making it all the way down here, if you have any questions or find anything that does not quite make sense, please feel free to reach out at matus@outlierventures.io. In future blog posts, we will explore the design space of governance and distribution mechanisms.
Join Base Camp
Outlier Ventures has been investing and accelerating the Web 3 ecosystem since 2013. In 2019 we launched Base Camp – an accelerator program for pre-seed startups operating in DeFi, NFTs and open data. We provide capital, help with your token design, access to our network of the best investors and founders of Web 3, back office support and mentorship.
What is more, in 2020 we started a decicated token launch program called Ascent where we help you launch, accelerate and scale your network.
Find out more about Base Camp and Ascent!
Contributors:
ZX Zhang (Protocol Labs)
Scott Collen (Outlier Ventures)
Vladimiros Peilivanidis (Outlier Ventures)
Roland Spencer (Outlier Ventures)