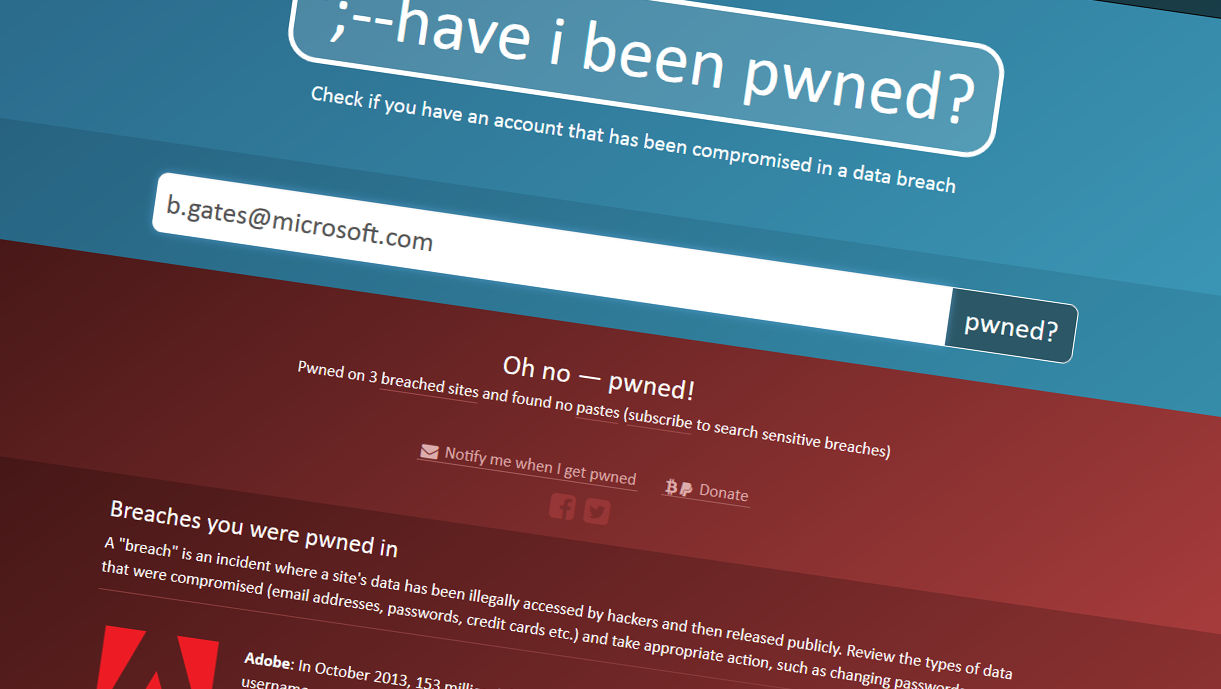
Dealing with identity of users is both a profound challenge and a promising opportunity for blockchain technology. We first explored identity in early 2015, when we identified 9 building blocks for a successful blockchain industry. So how are things mid-2016?
Tell me who you are
Let’s first see what we’re talking about. Identity is a complex concept. Your definition of “identity” might be “that which is contained in a passport”. It might be “your name and professional history”. It might be a person’s own perception of who they are, and it might be the perception of somebody else of who they are (like other people or a government).
This was ever so lucidly described by Vinay Gupta in his extensive piece Tell me who you are. To paraphrase Gupta:
You probably don’t know who you are. And if you do, you probably can’t tell me about it in a way that communicates it to me.
And we’re supposed to write software about this???!
Indeed we are. So how do we do that?
How online identity has been solved up to now
So how have builders of web services solved this? In the era of web applications, the “user” is generally something like this:
A single human,
- Who has a user name (petey89) and usually a full name (Peter Pancake)
- Who will, over time, have interactions with our system of which we store data
- Who has permissions within our system that enable them to access functionality and data
- Of whom we might expose data to other, connected systems and users as when relevant
The de facto standard to ensure that it is always this particular human that corresponds to our “user” has long been username/password/email. The human registers on our website with a chosen user name, something only they know (a password) and an e-mail address that we can send a recovery message to.
In “Web 1.0”, roughly the first decade of internet mass adoption, that information was usually accompanied by 30 other form fields containing highly personal information just to purchase a bag of pet food in a web store. High friction. Path dependence has very much had its effect here, with web forms initially being the digital version of the paper forms that we knew.
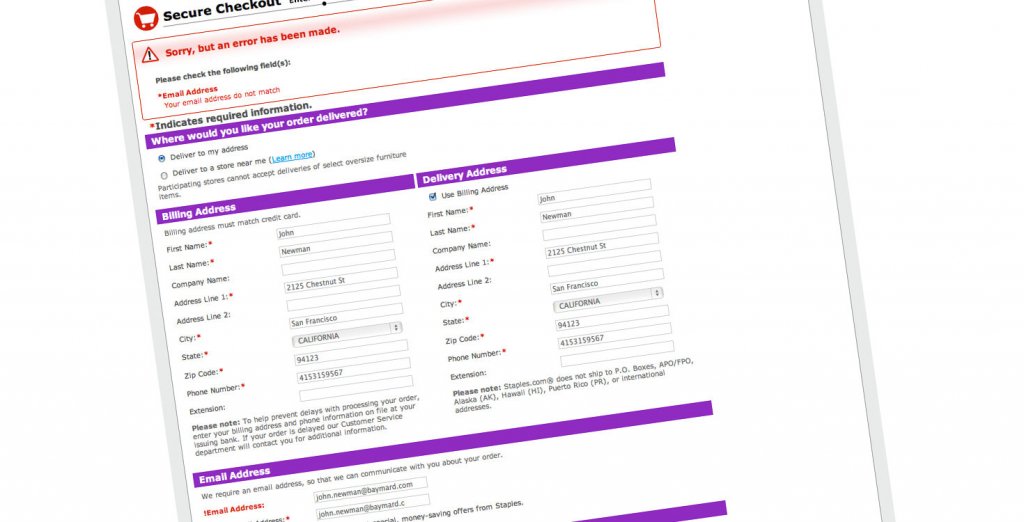
Web 1.0: So many questions
In “Web 2.0”, onboarding was made a lot smoother, and we got social logins with the likes of Facebook and Google. Recently we’ve seen many services improve their security by adopting 2-factor-authentication: the human possesses a device (usually a mobile phone) that produces a unique code on request, or receives a unique code through SMS. And with biometrics like fingerprint authentication becoming widely available on smartphones, it’s becoming increasingly smooth to make the “one human, one database record” connection in a secure manner.
Problem solved, right? Not entirely.
Where online identity gets it wrong
Authentication methods have evolved, but the core model of how online businesses deal with user identity hasn’t really changed that much. Businesses gather data of their users, store it in their databases, to the best of their abilities, and build a growing data set around this “identity”.
For cases where this model fits reality and things go to plan, it works well. But many things can and do go wrong:
- The human chooses a weak password or doesn’t manage their passwords well, with 55% of internet users using the same password for most websites.
- Attackers steal their recovery emails, which are in plaintext form and pass through many points in the network where they can be intercepted.
- Two-factor authentication gets compromised, for example through intercepting SMS messages or stealing/cloning mobile phones.
- The system database containing all user data gets compromised by attackers from outside or inside the organization.
Turning it around
Besides the weaknesses in securing this model of identity, do we even need it? For almost all cases of online services we need very little information from our users to be effective. And the information that we do need to provide, does not need to be related to previous purchase behaviour, interests or health situation. So why don’t we pursue a “need to know” model instead of a “gather as much data as possible” model?
For example, to complete a car rental request I should be able to prove “is able and allowed to drive a car” and “has paid the fee amount” and ideally I should be ready to go. Even insurance and liability is something that could be handled without providing the sensitive information in the first place. Think of putting my personal data in escrow with a third party that would only release it to the car rental in case something actually happens.
Decentralisation: complicating factor or solution?
Let’s make things a bit more complicated by shaking up the whole application model. Decentralised applications backed by blockchains introduce a different paradigm than both Web 1.0 and Web 2.0. No longer is there simply a centralised provider of services and users consuming those services. Users can become sovereign owners of their data and assets. Users can be machines. Users can, in the case of public blockchains, be pseudonymous.
In decentralised solutions, humans generally need to manage more security keys, not less, and the consequences of losing them are more harsh. When you forget your bank card PIN code, you go to the bank. When you forget the password of your Bitcoin private keys, there’s no one to go to, and the funds are just lost.
But there is promise in decentralised technologies. Principally, if identity information is stored and accessed in a decentralised manner, large-scale attacks are far less feasible. And considering that blockchains are effectively decentralised governance layers, there might be something there?
Promising approaches in decentralised identity
Indeed there is something there. A lot is happening in decentralised identity. A quick search for “Identity” on our blockchain startup tracker gives over 30 results. Some highlights:
- Blockstack, originally Onename, is one of the earliest to offer personal identities backed by a blockchain and have grown their user base to 50,000 registered identities.
- ShoCard have built a blockchain-backed digital identity platform that protects consumer privacy, optimised for mobile. They have successfully tested a prototype for air traveler identification.
- Evernym is building Sovrin, an open source sovereign identity platform on a dedicated, permissioned distributed ledger.
- Airbitz have pivoted from offering a Bitcoin wallet to a full-fledged edge security platform, encrypting data all the way from the end user while making it available as needed.
- uPort by ConsenSys has recently partnered with Microsoft to build an open source, self-sovereign, blockchain-based identity system. Not much details have been released, but much is to be expected from one of the biggest names in blockchain with one of the long-time biggest names in software. Combined with the recent acquisition of LinkedIn, can this make Microsoft the instant king of blockchain identity?
- Identi.fi have built a decentralised reputation system for people and machines, based on the principles of a Web of Trust. 2way.io are offering commercial services on top of Identifi.
Besides businesses being created, some interesting proof of concepts with decentralised identity have been developed:
- World Citizenship is an experiment by Chris Ellis “for anyone in the world to create their own Private Passport Service that can be used to validate and prove the existence of other persons using nothing but available tools”, using blockchain as
- Prescrypt by Radboud University, Deloitte and SNS Bank showed how blockchains can be used as a decentralised layer to securely share medicine prescription data with professionals. In this case a bank was used as the identity verifier.
Do you need to Know Your Customer?
Regulations from the “traditional” world of finance such as KYC (know your customer) and AML (anti money laundering) are a reality for any financial services business. In the eyes of many in the Bitcoin community, where pseudonymity is sacrosanct, they are seen as irrelevant and redundant. But regulations on financial services are a reality and they won’t suddenly disappear.
For the real-world applications ready for mass adoption we believe working with and integrating into existing regulatory structures is key to success. Moving from a paradigm where service providers store each and every detail of their customers in their own domain to one where end users are the sovereign controllers of their data can provide challenges to comply with such regulations.
A better way
Working with and not against regulation doesn’t mean that blockchain businesses should not challenge the status quo. KYC and AML are means to an end: preventing fraud, terrorism and other forms of crime. There might be better ways to reach that end that are less invasive of individual privacy and less straining on businesses.
Blockchain based self-sovereign identity systems could be such a better way. Instead of each business building their ever growing silos of sensitive customer data, businesses and regulators could work with a single, secure, shared ledger that manages access to relevant identity data. Regulation should grow hand in hand with this new technological reality. This could make it possible for smaller players to offer services that are as secure and as compliant as those of larger players, and give individuals much more privacy.
Where are we going?
The thinking and solutions for working with identity and blockchains have come a long way since early last year. We think decentralised identity has a great future.
We are hoping to begin a conversation that can benefit the community as a whole. As a next step, we are organising a virtual roundtable for blockchain CTO’s. Are you in a CTO or technically leading role in a blockchain company? Join in and continue the conversation.
This article is for information purposes only and does not constitute investment advice. This article does not amount to an invitation or inducement to buy or sell an investment nor does it solicit any such offer or invitation in any jurisdiction.
In all cases, readers should conduct their own investigation and analysis of the data in the article. All statements of opinion and/or belief contained in this article and all views expressed and all projections, forecasts or statements relating to expectations regarding future events represent Outlier Ventures Operation Limited own assessment and interpretation of information available as at the date of this article.
No responsibility or liability is accepted by Outlier Ventures Operations Limited or Sapia Partners LLP for reliance on the contents of this article.
Outlier Ventures is an Appointed Representative of Sapia Partners LLP, a firm authorised and regulated by the Financial Conduct Authority (FCA).