“What is the utility of your token?” is one of the first questions web3 projects hear from all sides. A well-designed token needs to provide value through the right incentives to all stakeholders, meaningful integration into the product or protocol, and be effectively distributed. The Token Utility Canvas helps break down the nebulous concept of “Token utility” into a systematic structure that allows teams to think through relevant aspects one by one.
A preliminary step: token discovery
Since 2018, when the 3D’s of token design was first published, the Outlier Ventures methodology and the tools we use to support teams with their token design have matured significantly. The Token Utility Canvas is one of a range of tools that help our team design effective tokens. It was developed by adapting the business model canvas, a gold standard of the lean startup methodology, to the decentralized paradigm of web3.
Before diving into the Token Utility Canvas, it is often helpful to prepare with a set of preliminary exercises. The token discovery workshop helps teams evaluate the potential for a token and gets them ready to fill out the Token Utility Canvas. The token discovery process answers the following key questions with 3 different exercises:
- What is the overall objective of the network or protocol?
- What are the most important stakeholders?
- How do the different stakeholders exchange value?
When it comes to the network objective, it is important to consider context, scope, and constraints, as well as defining criteria for success. We recommend representing stakeholders graphically, ordered according to their relative importance. The value exchange between stakeholders should be described in terms of the benefits for each stakeholder, as well as the mechanisms through which they exchange value.
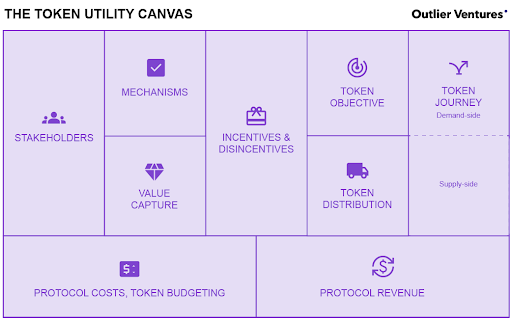
Breaking down the Token Utility Canvas
Once the token discovery step has been completed and we have clarity on objectives, stakeholders, and value exchange, we are ready to fill out the Token Utility Canvas. We will go through the different sections of the Token Utility Canvas one-by-one to provide more context on how the tool is used.
Stakeholders
The first section of the Token Utility Canvas is to be populated with the outcomes of the stakeholder analysis conducted in the token discovery phase. Rather than a business serving a single customer, web3 networks and protocols often are n-sided networks, where different actors interact to create value. A typical list may include different types of users, providers of a decentralized service, investors, as well as the community at large. It is recommended to list them in order of importance.
Mechanisms
Mechanisms describe how the different stakeholders use the token to interact with one another and with the core product/protocol. Examples include using the token as a means of payment or a representation of a certain resource or as a commitment or collateral (e.g. different staking or locking mechanisms). The token may also be used for different signaling modalities (e.g. curation or governance), or for the right to provide work. The mechanisms are quite different from one project to another and will depend on the overall network objectives, as well as the value exchange between different stakeholders. What they all have in common is that the token mechanisms provide the means for the stakeholders to coordinate in a decentralized manner. When filling out the canvas for the first time, we encourage teams to list different ideas and then help refine them in discussion with our token design experts.
Incentives and disincentives
How can we coordinate the different (often anonymous) stakeholders if we don’t have contracts or any sort of formal control like we would in a corporation? Carrots and sticks, is the answer. Incentives and disincentives are created through the utility mechanisms, and modulate the behavior of the different stakeholders by rewarding and punishing certain actions. The first example of such a crypto-economic system was Bitcoin, where miners are rewarded with BTC for correctly running the consensus (incentives) and forgo that revenue when they are on the wrong chain (disincentives). Since Bitcoin, we have seen a huge proliferation of similar mechanisms to coordinate a range of different stakeholders. A common pattern is to require collateral in the native token for the right to provide work of different kinds. If the work is done correctly, rewards are earned. In the case of faulty work or even an attack on the network, the collateral can be confiscated (“slashed”). It is important to consider incentives and disincentives for all major stakeholders, and systematically thinking through this helps to fine tune the mechanisms used.
Token objective
The token objective can be derived from considering both the overall network objective conducted in the token discovery phase, as well as the incentives/disincentives section prior to it in the Token Utility Canvas. The token objective often includes the coordination of the different stakeholders to produce value as a network, whether that happens on the infrastructure or application layer. On top of that, the native token is also frequently used to govern the protocol in a decentralized manner. Governance is usually conducted under the umbrella of a DAO that allows token holders to come to agreement on the mechanisms and parameters used, manage the treasury, and decide on the future of the protocol. At Outlier Ventures, we have a different process to structure governance: there are workshops and tools specifically focused on that topic, and a governance specialist that supports teams for which it is a priority.
Token journey
This section of the Token Utility Canvas helps teams think through how the most important stakeholders would acquire and then use tokens. Ideally, teams would consider the full journey those stakeholders will go through, which helps identify potential points of friction. For example, a user could earn their token through user rewards or an airdrop, or need to first acquire it before being able to use the protocol. Sometimes, the token is not required for basic users but unlocks more advanced forms of participation. While some stakeholders will only go through a part of that journey and then drop off, others will get more involved over time (e.g. take on other roles, participate in governance, etc.). As a result, the token journey can also be thought of as a funnel with different conversion and churn rates between the different levels of engagement. Often, distinguishing the token journey between demand and supply side makes sense, but this depends on the specifics of a project (sometimes, this distinction is discarded altogether or replaced with a more suitable one).
Value capture
If the token is used to capitalize the network by using it as an instrument for fundraising (whether from private investors or with a public sale), to determine ownership, and to set long-term incentives for key stakeholders including the team, it needs to capture value. Value capture answers the question “If this project is successful, why would the token be valuable?”. The market price of a token is always determined by the supply and demand at any given time. As a result, a token that captures value needs to create sustainable demand for the token, e.g. because it is needed to use the network or clear benefits can be unlocked by being a token holder. Properties of the supply dynamics are at the heart of this section, for instance whether there is a fixed, inflationary or even deflationary supply of the token. For instance, mechanisms adapted from traditional finance that rely on programmatically buying back of tokens, either for redistribution (“buyback-and-make”) or permanently removing them from supply (“buyback-and-burn”) provide different ways of value capture. Additionally, mechanisms like staking that remove circulating supply while giving out continuous rewards to stakers indirectly support the value capture of a token.
Token distribution
Token distribution concerns how the supply of the token is split up and distributed. This includes the release schedules (vesting) for investors and the team, where 2-5 years of locked up tokens have become standard to ensure alignment. Token distribution also concerns the mechanisms with which the token is launched initially, as well as distributed over time. For launching a token, a wide range of mechanisms is available: airdrops to early users, pre-sales to private investors, public sales with different pricing mechanisms (simple priced sales, vs. auctions or liquidity bootstrapping pools), or direct listings on exchanges. When it comes to distribution over time, projects can either choose to distribute tokens to their users either initially (e.g. conditional airdrops or temporary reward campaigns) or continuously (based on usage numbers).
Protocol costs (token budgeting)
Each of the distribution mechanisms outlined above will require its own pool of tokens. For that reason, it is important to budget the initial token supply as well as any ongoing flows from inflation or buybacks. In this section, there is just enough space to make an initial list of different “budget items” for which tokens are needed. Outlier Ventures experts work together with teams to budget tokens quantitatively in a spreadsheet format.
Protocol revenues
Finally, the protocol revenues section describes the financial flows that accrue on a protocol or network level, as opposed to stakeholders directly. Often, there are usage fees that flow into the treasury of the project. Whether the fees are implemented from the beginning or only inserted at a more mature stage is a strategic decision that depends on many factors. In the case of inflationary models, there are also possible revenue flows from these new token emissions. Sometimes, destroyed tokens in a burn-and-mint model are also counted as indirect protocol revenues, since these value flows indirectly accrue to token holders.
A starting point for developing token utility
The Token Utility Canvas provides a great starting point and an overview of the most relevant aspects of token design. However, the process only starts here and it generally takes 3-6 months to design and plan the launch of a token fully. Each of the different sections unfolds into more detailed discussions and decisions. For instance, deciding between different mechanisms to ensure both utility and value capture usually requires an analysis with a token design specialist where different options are evaluated. The same goes for distribution strategies and governance structures. At Outlier Ventures, we support this process with regular 1-1 calls with different experts, as well as workshops that go deeper into different topics (e.g. mechanisms, distribution, structuring, liquidity, governance). After filling out the Token Utility Canvas, teams start working on value flow diagrams that summarize the token utility graphically for their documentation, and on a spreadsheet that plans the genesis allocation and distribution. As a team gets closer to launching their token, a specialized token engineer helps with modeling projected supply dynamics quantitatively. We love to keep up with new mechanisms in token design at Outlier Ventures and continue developing our tools to best support founders on the exciting journey of launching their own token.




